Are you looking for the best hidden spy app for Android & iPhone?These best Spy APPs can monitor anyone's smartphone activity such as call logs/recordings, owner's social media, SMS messages, and even background recordings around the phone. With this spyware, children, spouses, employees can be tracked and protected from illegal information and illegal actions.
Safety
What secrets are hidden behind the dark web: the difference from the deep web
The dark web is not as scary as you might think. This article explains the difference between the dark web and the deep web, and how to use them.
When you look up at the sky, what do you see? A blazing sun, a cloud, and the occasional plane. The sky doesn't seem to have much, but there are more things that the eye can't see, far beyond our field of vision.
Why you need a VPN privacy protection tool to surf the Internet at home
Governments, advertisers, and even hackers may try to monitor your browsing history. Without a VPN, your internet service provider (ISP) could log your online activity and sell it to the highest bidder. So do you need a VPN?
8 Scenarios When VPNs Are Highly Recommended: Stay Safe Online
You probably don't want someone staring at you through your home window to see what you're doing. But did you know that strangers can peek through your browser window? It happens more often than you might think. This is why your VPN should always be turned on.
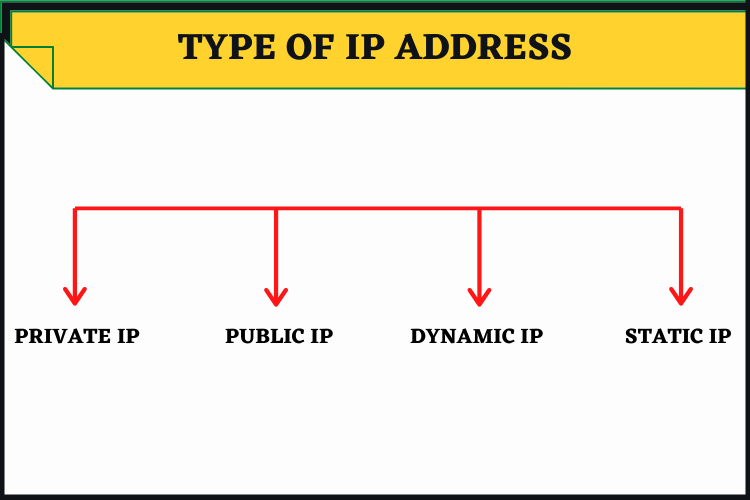
Types of IP Addresses: All You Need to Know
IP addresses allow Internet-connected devices to communicate with web servers. However, there are many types of IP addresses. Do you know the main difference between private and public IP addresses or static and dynamic IP addresses?What is a dedicated IP, do you need one? Read on to learn more about the different IP address types and their uses.
6 Best VPN Protocols
Not all VPNs are created equal. Depending on its VPN protocol, it may have different speeds, features, and even security and privacy holes. This article examines the major VPN protocols so you can choose the one that's best for you.
What can others do with my IP address
Your IP address is essential to sending and receiving information online. However, if hackers know your IP address, they can use it to obtain very valuable information, including your location and online identity. Using this information as a starting point, they could hack your device, steal your identity, and more.
NordLynx Protocol – Fast and Secure VPN Connection Solution
What is NordLynx and how does it work?
The NordLynx protocol is an encryption system that protects your privacy when you use a VPN. This is a process that encrypts user data as it travels to and from the VPN server, so no one can intercept and view it in transit.
What is NAT - Gatekeeper of the World Wide Web
The Internet is very complex, and its complexity is similar to that of a highway system. However, the data managed to find it. NAT is a tool that helps not lose data. Let's take a look at how it works and what its main purpose is.
The 22 Most Practical Special Spy Gear Your Life Can Buy
Many real-life occupations do require stealth and covert operations, such as bounty hunters, law enforcement officers, private investigators, and journalists, etc., using many espionage tools to get the job done. Whether gathering intelligence late at night, passing sensitive documents, or having a conversation with someone special, this list of gadgets keeps you safe by enhancing your eyesight (like night vision goggles) and masking your voice.